Making a Single Connector Carry Power, Data, and Trust
Connectors are often discussed in terms of pin count, current rating, or mechanical life. Those are important—but they’re not the reason connectors fail products.
In real systems, connectors fail when they are asked to carry too many assumptions without being designed to enforce them.
A single connector today is expected to:
- Deliver power from unknown sources
- Carry data across multiple operating modes
- Tolerate hot-plugging, mis-plugging, and cable abuse
- Survive partial insertion, wear, and contamination
- Behave safely before software is alive
- Recover cleanly when things go wrong
In other words, a connector is no longer just an interface. It is a system boundary.
At Hoomanely, we treat shared connectors as something more demanding: a place where power, data, and trust intersect. Designing that intersection well is the difference between a system that feels resilient and one that feels fragile—even if both “meet spec.”
This article explores what it takes to make a single connector reliable not just electrically, but behaviorally.
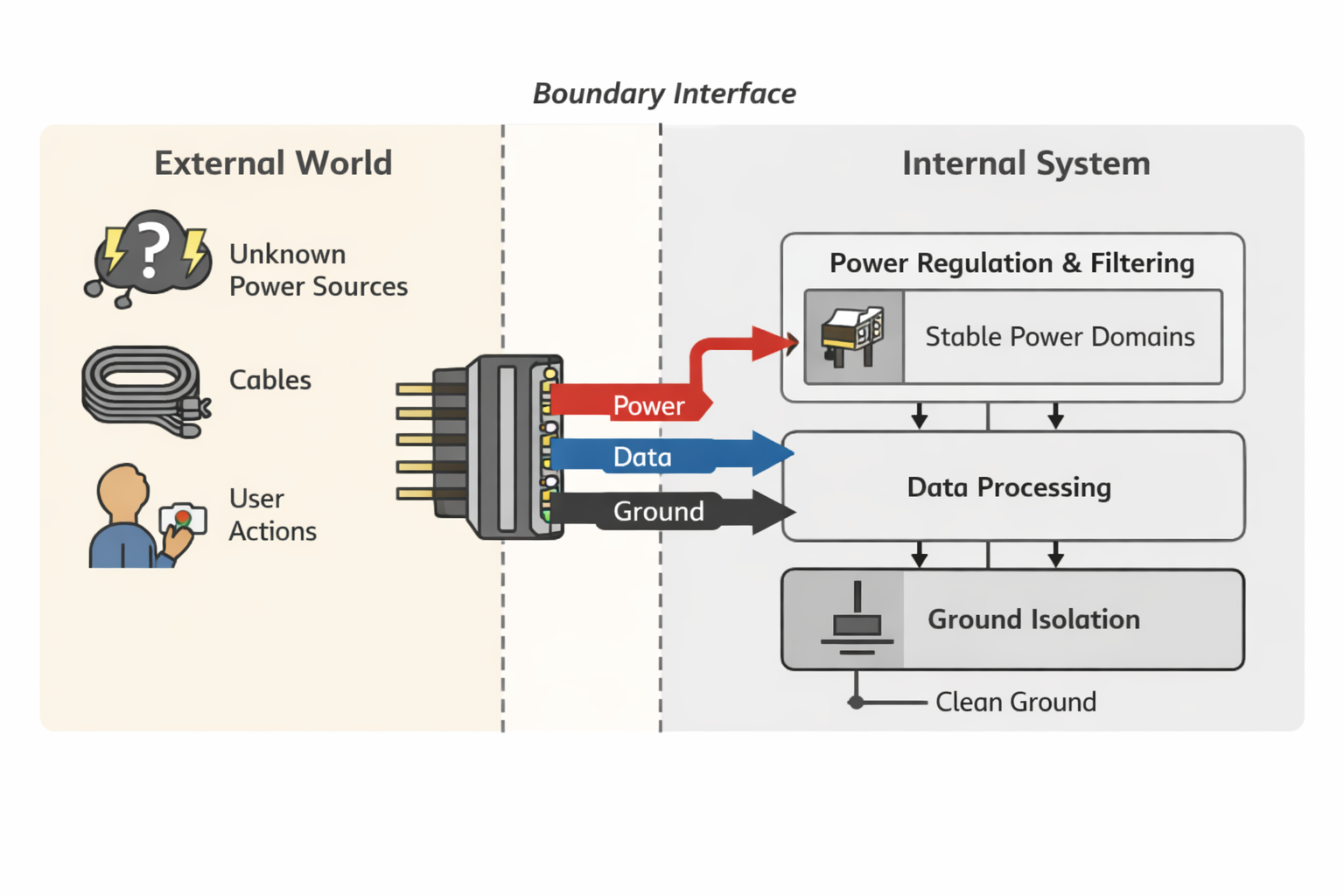
The Connector Is Where Assumptions Collide
Every connector sits between two worlds:
- What the system expects
- What the environment actually delivers
Those worlds rarely match.
On one side, designers assume:
- Power arrives within a reasonable range
- Data lines are used correctly
- Ground is solid
- The cable is intact
- The insertion sequence is clean
On the other side, reality delivers:
- Cheap cables with poor shielding
- Slow or collapsing power sources
- Partial insertions
- Reversed or worn connectors
- Users who plug things in “just to try”
The connector is the only place where these mismatches must be resolved—often before software can intervene.
If the connector does not enforce boundaries, the rest of the system absorbs the chaos.
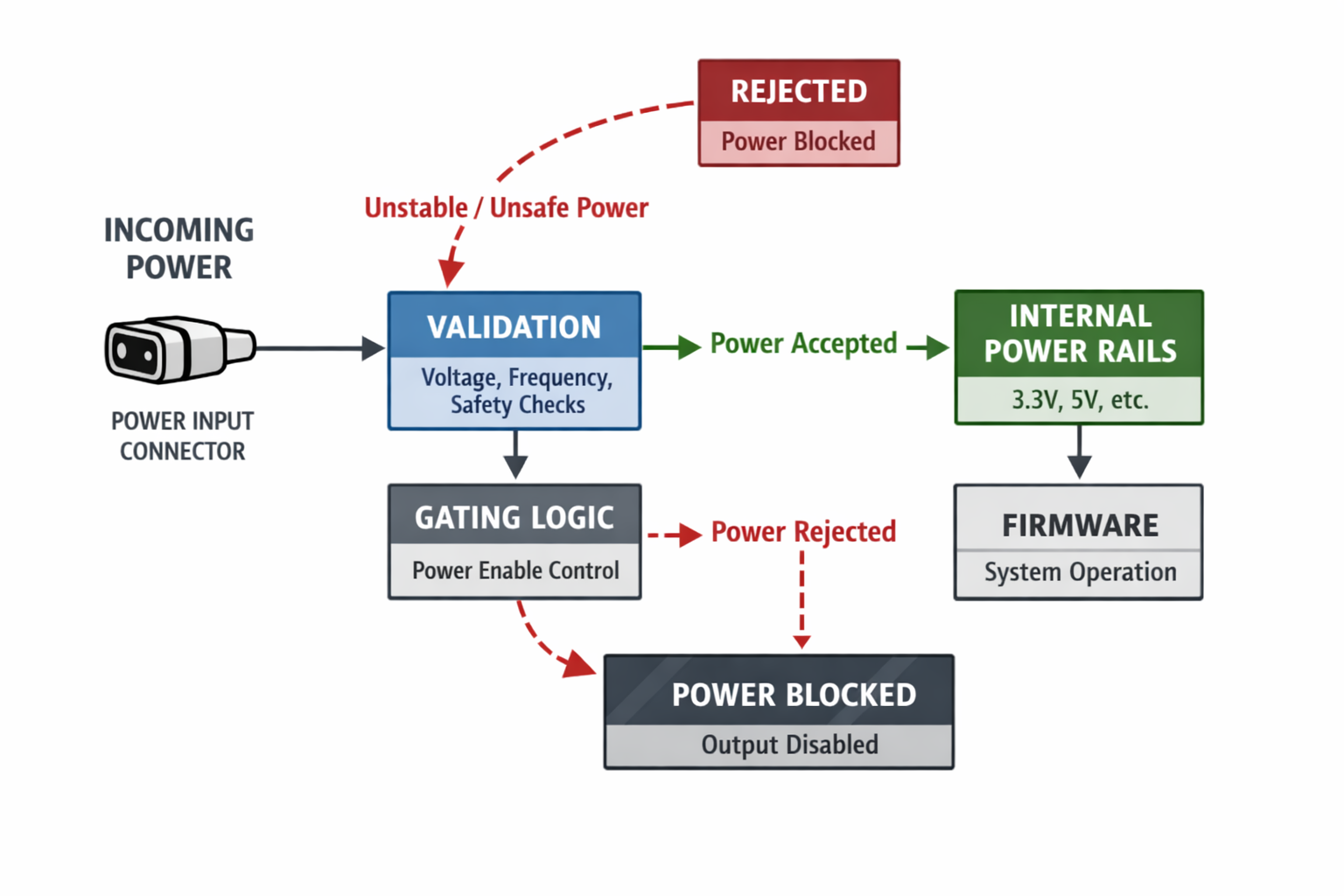
Power Cannot Be Trusted by Default
The first job of a shared connector is power entry. The mistake many systems make is treating incoming power as inherently valid.
In practice, power arriving at a connector is:
- Noisy
- Poorly regulated
- Sometimes absent
- Sometimes excessive
- Sometimes reversed or transient
A connector that carries both power and data must therefore negotiate power, not assume it.
This negotiation happens entirely in hardware:
- Power must be gated until validity is established
- Downstream rails must be protected from upstream uncertainty
- The system must remain safe even if data activity begins early
Crucially, this must work before firmware exists. If safe power depends on software configuration, then corrupted firmware becomes a physical risk—not just a functional one.
When power trust is enforced at the connector boundary, the rest of the system can behave predictably. When it isn’t, every downstream decision becomes defensive.
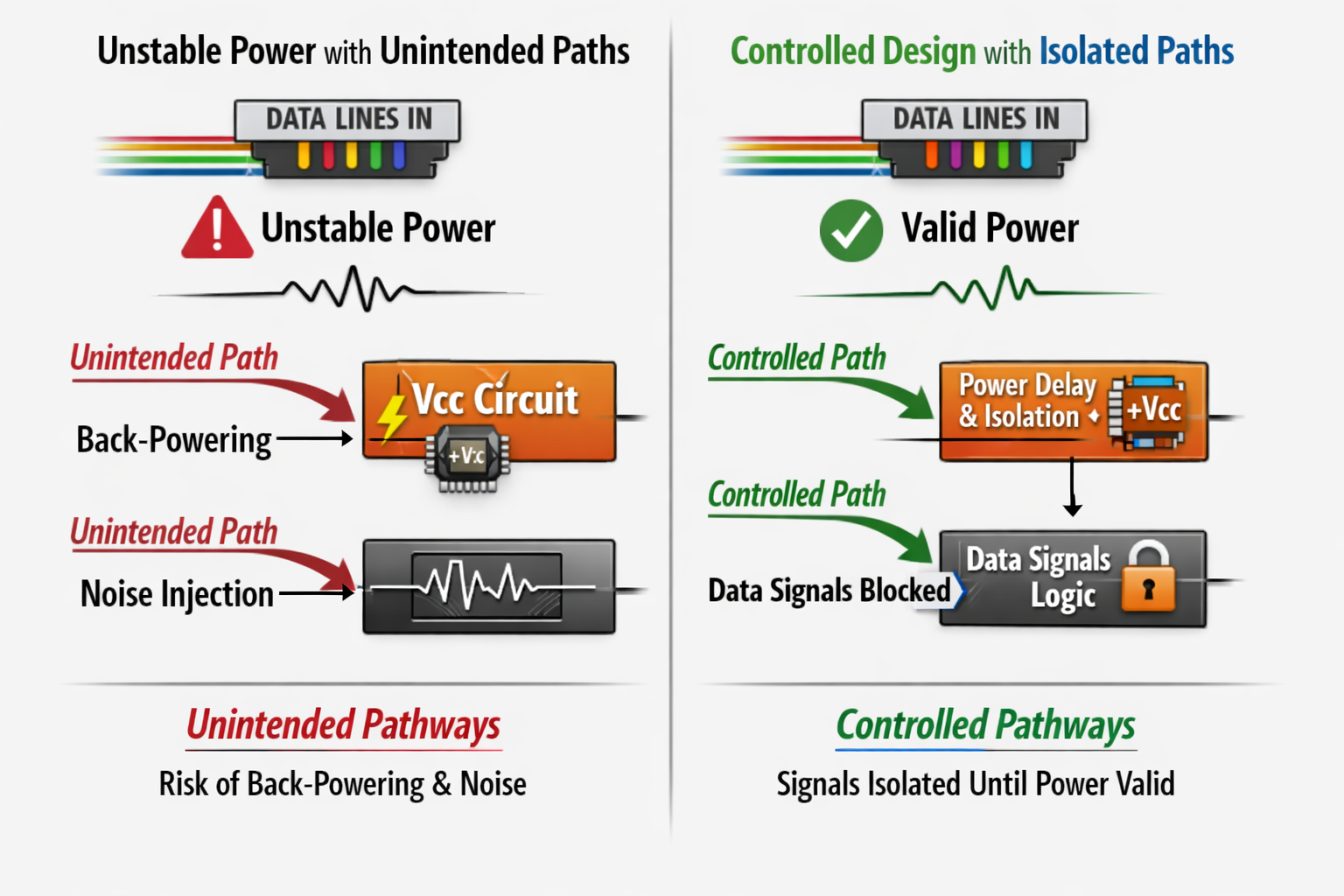
Data Lines Are Not Innocent Bystanders
Data pins are often treated as passive passengers on a connector whose primary job is power delivery. This is a dangerous oversimplification.
Data lines:
- Can back-power internal domains
- Can inject noise into sensitive rails
- Can become unintended ground paths
- Can misbehave when referenced to unstable power
In mixed-use connectors, data integrity is inseparable from power integrity.
A trustworthy connector design ensures that:
- Data cannot energize the system unintentionally
- Data lines are quiet when power is unstable
- Reference paths are well defined even during transients
This often means intentionally delaying or isolating data paths until power conditions are sane—not because data is fragile, but because it is powerful.
Trust Is About What Happens When Things Go Wrong
Most connector designs work when everything goes right. The question is what happens when things go wrong.
Consider common failure modes:
- Cable inserted halfway
- Power source collapses mid-transaction
- Data lines toggle before ground settles
- Connector wears unevenly over time
- User hot-plugs repeatedly under load
A connector that carries trust must handle these conditions gracefully.
That means:
- No uncontrolled current paths
- No undefined logic states
- No reliance on timing coincidences
- No permanent damage from momentary misuse
Trust is not about preventing all failure. It is about containing failure so that recovery remains possible.
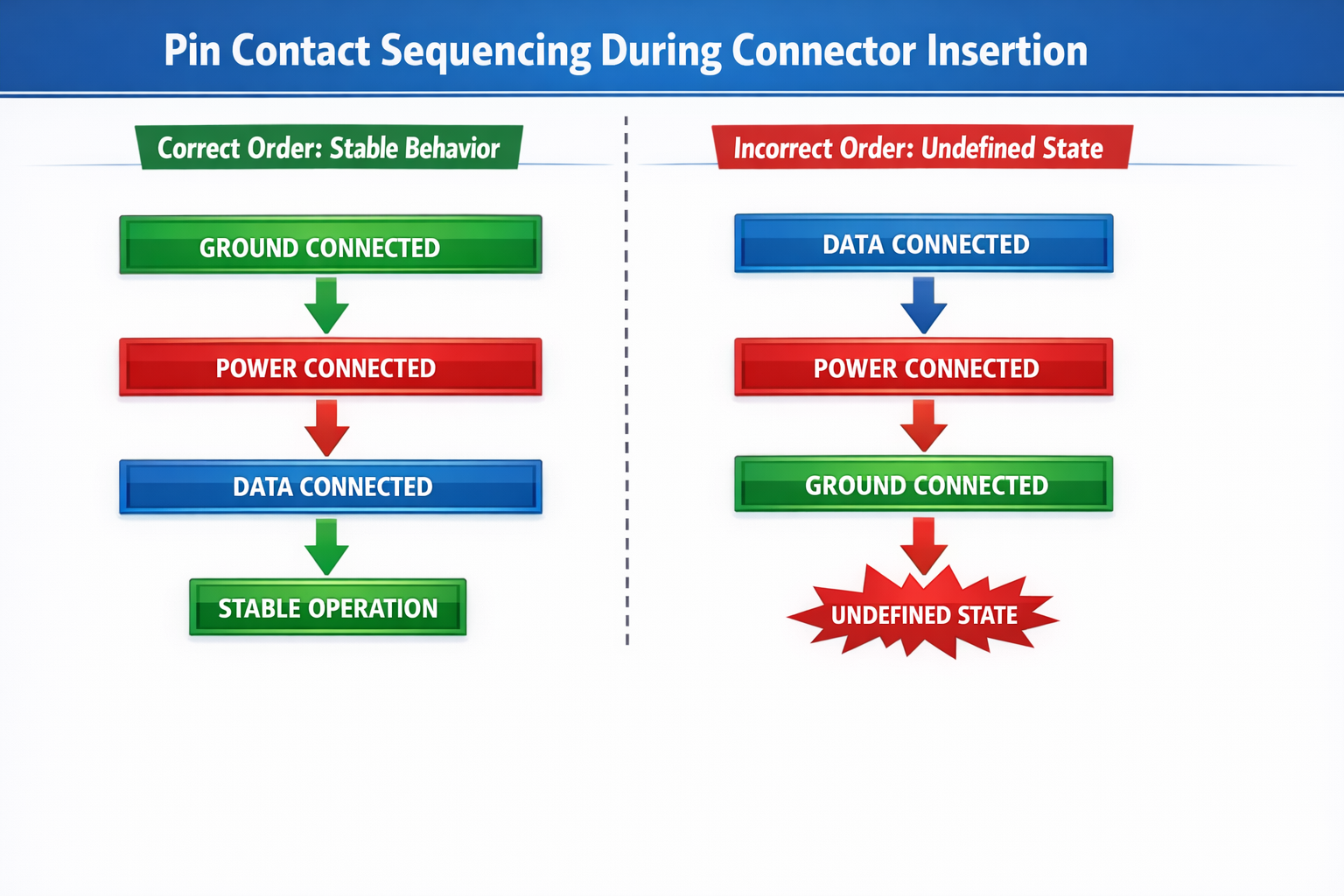
Ordering Matters More Than Speed
One of the most subtle aspects of connector design is ordering.
Which pins make contact first?
Which signals become active first?
Which domains reference which grounds?
These questions are often left to mechanical drawings or connector vendors. In reality, they define system behavior.
In shared connectors, ordering determines:
- Whether data lines see valid references
- Whether power rails rise cleanly
- Whether internal protection behaves as intended
A system that enforces ordering electrically does not care whether insertion is slow, fast, or uneven. It behaves the same way every time.
This predictability is what makes systems debuggable—and trustworthy.
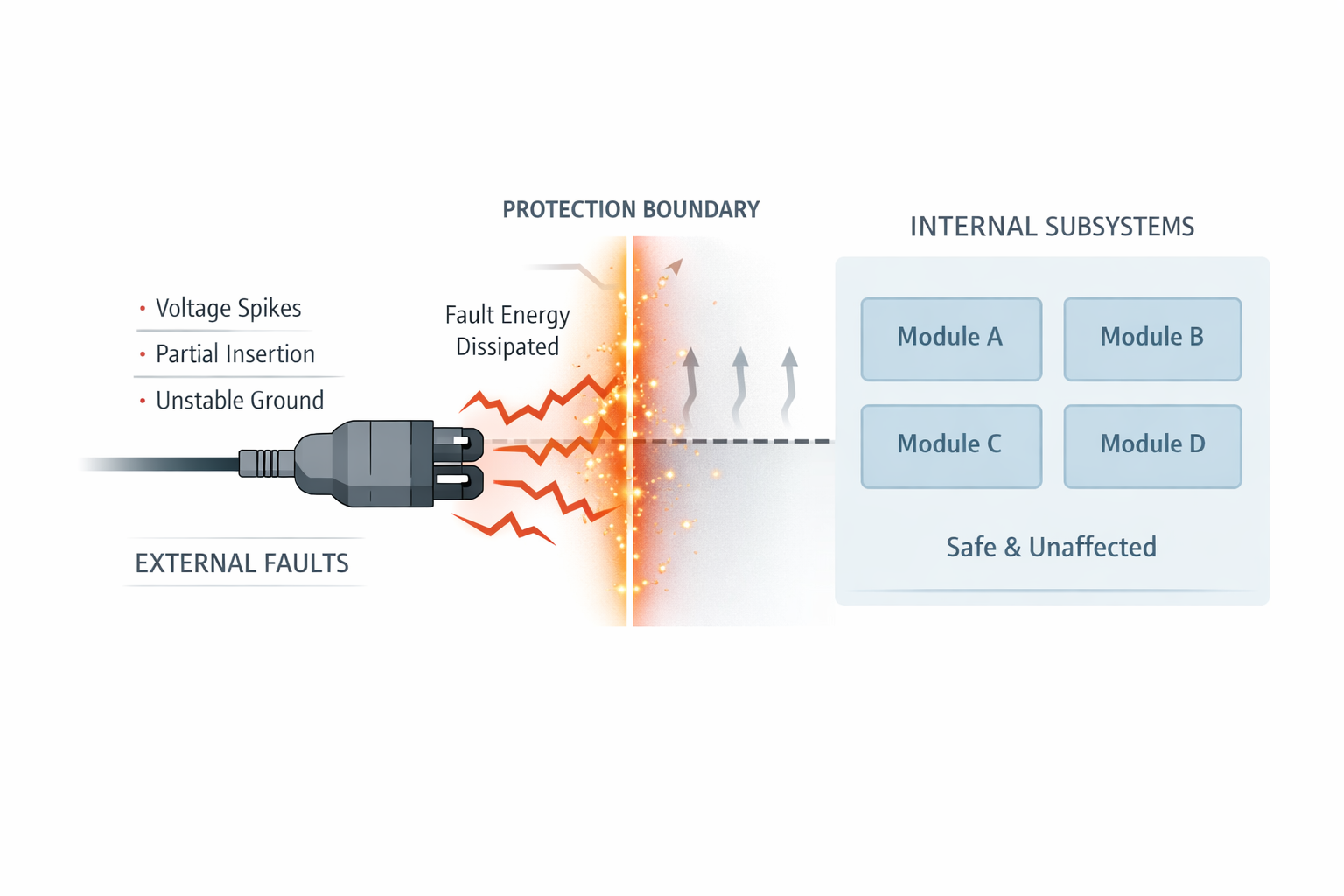
The Connector as a Fault Containment Boundary
When a fault enters through a connector, it should stop there.
This sounds obvious, but many systems allow connector-originated faults to propagate deeply:
- Power glitches ripple across rails
- Data contention corrupts internal state
- Ground bounce creates intermittent failures
- Protection triggers reset loops
A well-designed connector boundary treats external faults as foreign events that must be sanitized before entering the system.
This is not achieved with a single protection device. It is achieved with layered intent:
- Electrical gating
- Reference isolation
- Defined default states
- Clear power ownership
The connector becomes a firewall—not just a plug.
Manufacturing and Field Reality
Connectors are also where manufacturing and field behavior intersect.
On the factory floor:
- Assemblers plug and unplug repeatedly
- Power sources are shared and imperfect
- Units are tested in partial configurations
In the field:
- Cables are reused
- Power sources vary wildly
- Users experiment
A connector that carries power, data, and trust must tolerate both worlds without requiring special handling or tribal knowledge.
This reduces:
- Factory test failures
- Field returns attributed to “intermittent issues”
- Support cases that cannot be reproduced
The more self-describing and self-protecting the connector boundary is, the less institutional memory is required to operate the system safely.

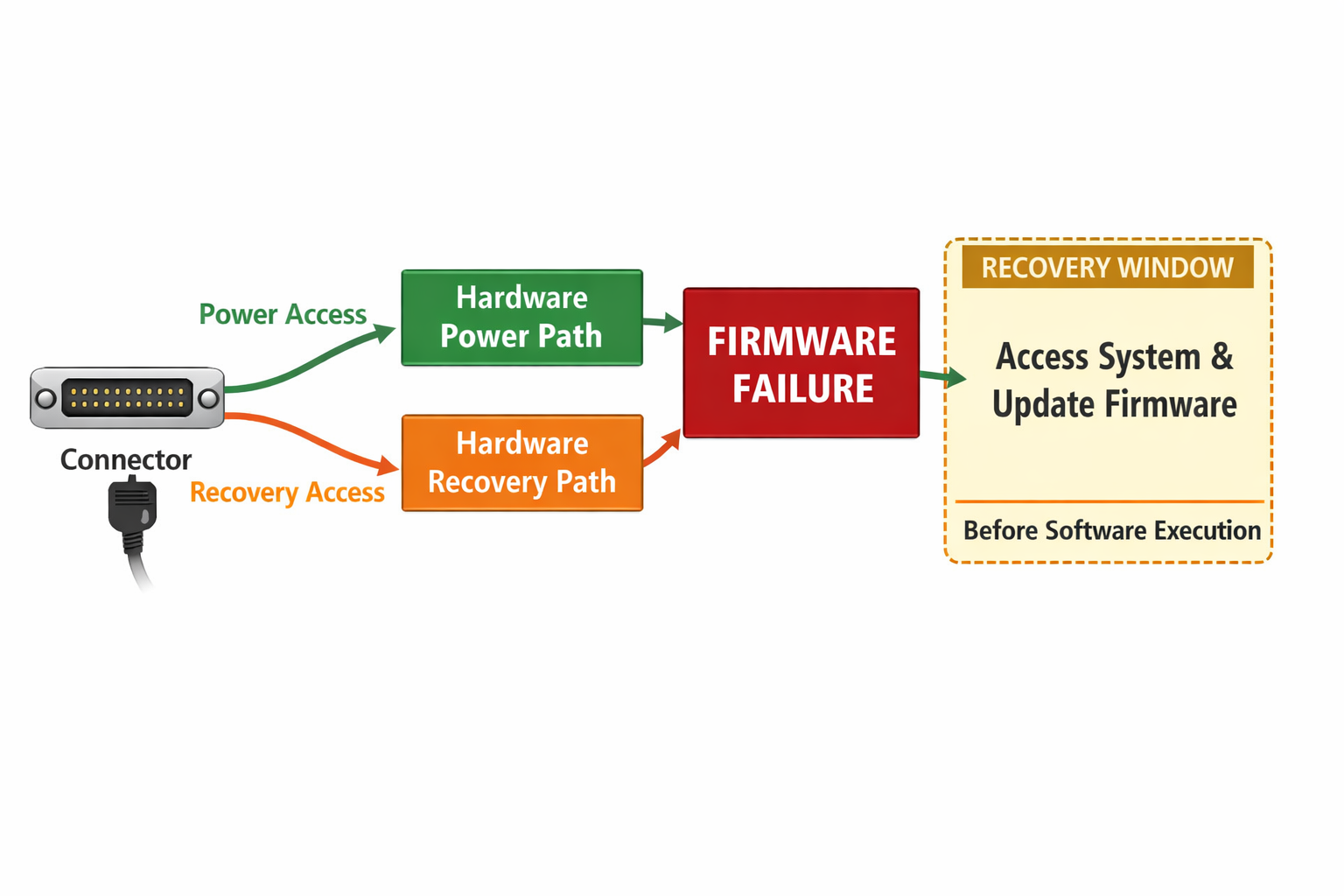
Trust Extends to Recovery
Eventually, something will go wrong.
Firmware may fail.
Storage may corrupt.
A peripheral may misbehave.
In those moments, the connector often becomes the recovery path:
- For reflashing
- For diagnostics
- For controlled power cycling
If the connector’s behavior depends on healthy software, recovery becomes impossible precisely when it is needed most.
By contrast, when the connector enforces safe power and stable signaling independently, recovery remains available—even in severely degraded states.
This is where trust becomes tangible. Not as a feature, but as the absence of panic.
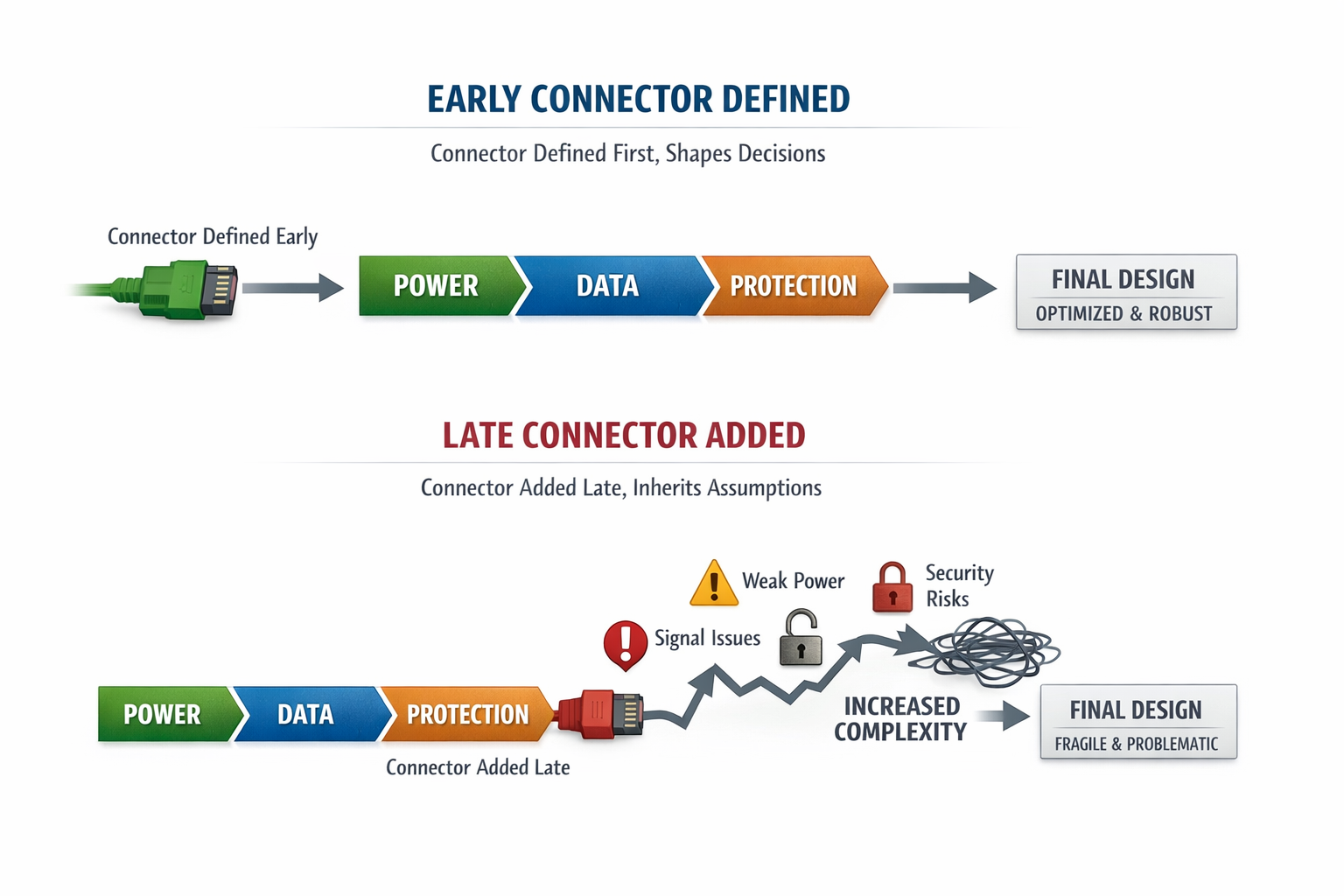
Designing the Connector Early Changes Everything
One of the most common mistakes is designing the connector late.
When connectors are added after the system architecture is “done,” they inherit assumptions rather than define them. Power paths are repurposed. Data lines are overloaded. Protection becomes reactive.
At Hoomanely, we treat shared connectors as architectural primitives. Their behavior is defined early, before feature decisions harden.
This forces clarity:
- What power is allowed
- When data is valid
- How faults are handled
- How recovery works
Once those rules exist, the rest of the system aligns naturally.
Power, Data, and Trust Are Inseparable
A connector that carries power and data but not trust will eventually betray the system.
It may work in the lab.
It may pass initial tests.
It may even ship successfully.
But over time—under wear, misuse, and edge conditions—it will expose assumptions that were never enforced.
By designing connectors as places where power, data, and trust are intentionally negotiated, systems become calmer. Failures become contained. Recovery becomes routine.
The connector stops being a liability and becomes an ally.
And that is the difference between a product that merely functions and one that earns confidence every time it is plugged in.




