Designing Safe and Predictable BBLayers for CM4

Yocto gives embedded teams extraordinary power but it also gives them extraordinary power to break their own systems in subtle, silent ways. Anyone who has shipped a commercial Linux-based device knows this: your build system becomes part of your product’s architecture. If the layering model is unstable, everything above it inherits that fragility.
At Hoomanely, we build a multi-device pet-care ecosystem powered by modular SoM-driven architectures EverBowl, EverSense trackers, EverHub gatewaysand Yocto is the glue that ensures consistent behavior across those platforms. The challenge: as we scale machine configurations and SoM variants , we must prevent hidden overrides, version drift, and bitbake “shadowing traps” long before they hit a build server.
This article explains how to design a safe, predictable, conflict-free BBLayers model for CM4 using meta-raspberrypi and a custom meta-everos layer. Instead of a tutorial, this is a deep architecture explainer:
Problem → Why It Matters → Architecture → Implementation → Real-World Usage → Takeaways.
1. The Problem: Layering That Looks Fine… Until It Isn’t
Yocto layering issues tend to hide quietly until they explode loudly.
Bitbake will happily:
- Let two layers define the same recipe but choose one via priority rules you forgot existed
- Allow unintentional
FILESEXTRAPATHSshadowing - Accept a machine config that partially inherits from another and silently drops critical includes
- Permit appending
.bbappendfiles that never actually apply - Build an image that “works” yet embeds mismatched kernels, firmware, or BSP patches
When working CM4-based systems during prototyping, the risks multiply. meta-raspberrypi is opinionated—kernel fragments, GPU stack, firmware blobs, boot partition structure—which means your own layer must cooperate, not compete.
This is where many anti-patterns appear:
- Putting BSP overrides in your app layer
- Adding bbappends without knowing bitbake’s search order
- Mixing machine configs across layers
- Overriding Raspberry Pi boot logic without explicitly intending to
When scaling to multiple SoMs as we do at Hoomanely—this gets even trickier. A tracker, a bowl, and an edge hub all want the same consistent EverOS base, but their hardware differs drastically.
2. Why It Matters: Stability > Features
A deterministic Yocto layering model gives three critical properties:
1. Predictability
When a recipe is overridden, you know who did it and why.
No “ghost appends,” no mystery patches.
2. Portability
The same EverOS layer works across CM4 today and another SoM tomorrow.
This matters deeply for our pet-care ecosystem, where EverBowl, EverSense-style devices, and EverHub share behaviors even though each has different sensing and connectivity profiles.
3. Scalability
New machine variants, new SoM families, new products—none require re-inventing the layering model.
You simply add new conf/machine/*.conf files that slot cleanly into the existing architecture.
A fragile setup makes this impossible.
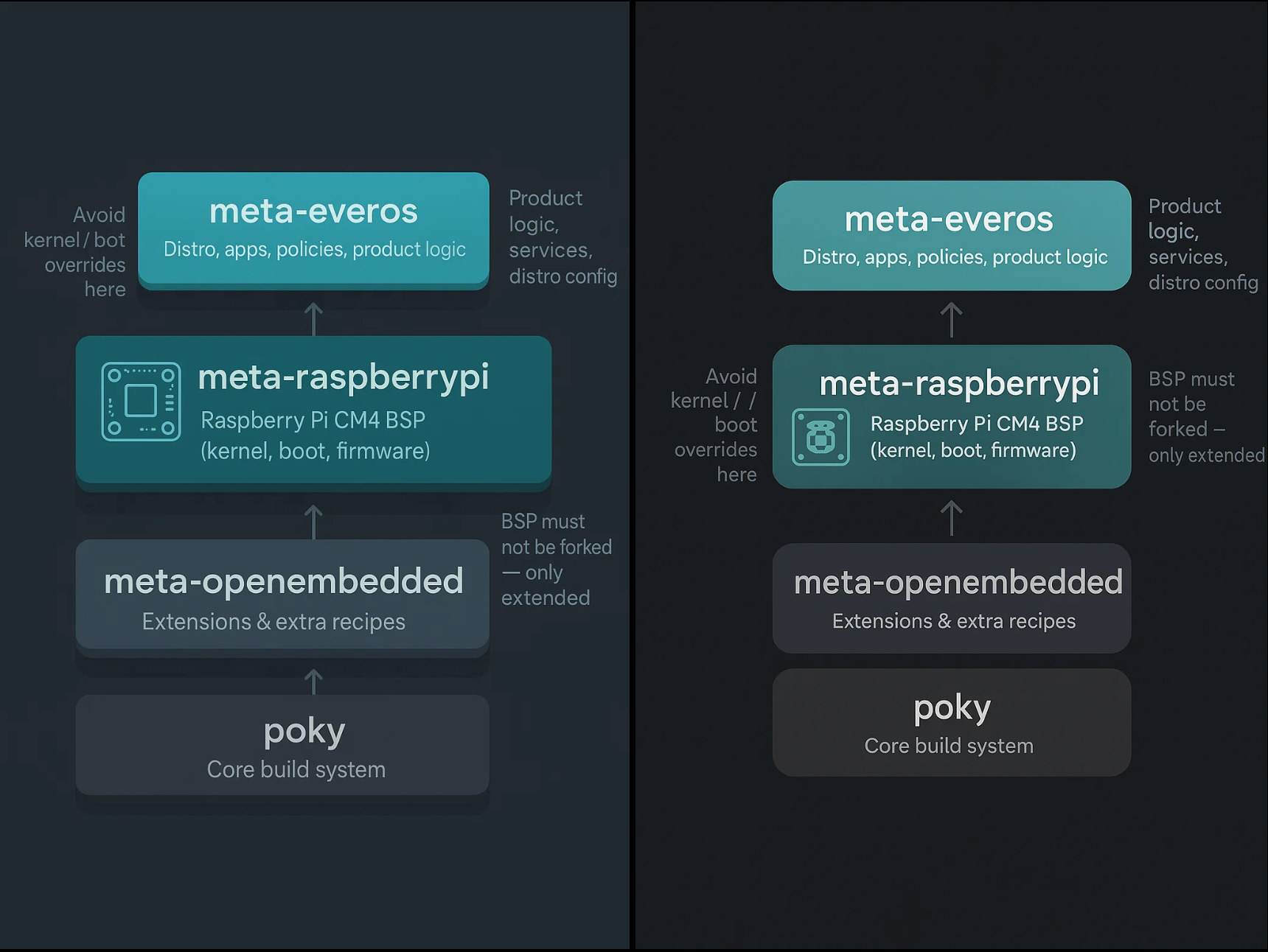
3. Architecture: A Clean, Conflict-Free Layering Model
A predictable BBLayers structure emerges from three principles:
Principle 1 : BSP Belongs to the BSP Layer
meta-raspberrypi must own all CM4 BSP responsibilities:
- Kernel + device-tree + overlays
- Bootloader chain
- Firmware blobs
- GPU stack
- Config fragments
- RPi-specific utilities
Your custom meta-everos must never override these unless explicitly intended.
Good structure:
poky/
meta-openembedded/
meta-raspberrypi/
meta-everos/Bad structure:
meta-everos/bsp/
meta-everos/linux/
meta-everos/boot/
You don’t fork the BSP; you extend it.
Principle 2 : Product Logic Lives in meta-everos
everOS should only define:
- Common distro configuration (
everos.conf) - Product-agnostic policies (logging, security posture, update flow)
- Application stack (services, containers, telemetry agents)
- Firmware helpers
- Unified filesystem layout
- Device orchestration logic
This ensures that EverSense-style trackers, EverBowl’s vision/sound pipeline, and EverHub’s edge compute all share a consistent OS base.
Principle 3 : Machine Configs Must Be Pure, Single Purpose
Each SoM or device gets:
meta-everos/conf/machine/<machine>.conf
A machine file must not contain:
- Random distro overrides
- Kernel hacks
- Bootloader policies
- Application-level decisions
Machine configs should only define:
- SoM’s hardware characteristics
- Image format
- Required features
- BSP layer includes
This keeps all devices aligned especially important when you run multiple SoMs across the pet-care ecosystem.
4. Implementation: Designing everOS for CM4 the Safe Way
Now let's walk through how to implement a layering model that avoids foot-guns.
A. Define a Stable Distro Configuration
meta-everos/conf/distro/everos.conf should include:
- Inheritance from Poky
- Security posture
- Package selection policy
- Update mechanism hooks
- Filesystem decisions
Keep it clean and generic.
No CM4-specific logic.
B. Use bbappend Sparingly and Explicitly
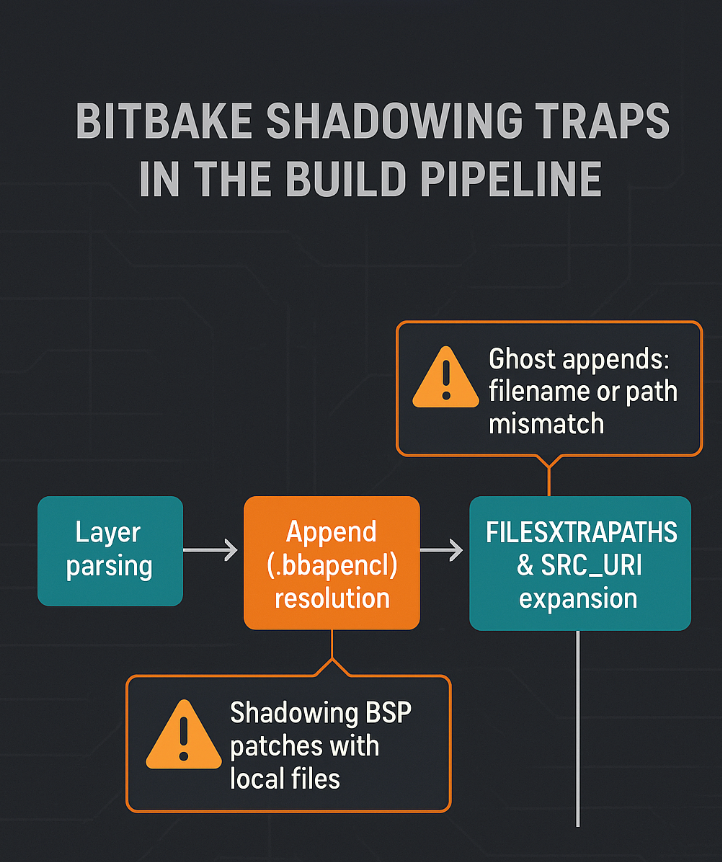
A common pitfall: bbappends that silently fail to apply.
To avoid this:
- Mirror directory structure exactly
- Avoid globbing filenames
- Add comments in each bbappend explaining the override’s intent
- Verify with
bitbake-layers show-appends
Good:
recipes-core/systemd/systemd_%.bbappend
Bad:
systemd.bbappend
C. Use a Machine Include Hierarchy
This guarantees portability across SoMs.
Example:
conf/machine/include/everos-base.inc
conf/machine/cm4.conf
conf/machine/everhub-gateway.conf
conf/machine/eversense-tracker.conf
conf/machine/everbowl-edge.confeveros-base.inc defines shared features:
- journal settings
- rootfs layout
- Wi-Fi + BT support
- Telemetry services
Each device config only adds:
- SoM type
- Image type
- Additional hardware flags
This structure saved us from many silent regressions across the Hoomanely ecosystem.
D. Protect Against Shadowing Traps
The two big offenders:
- FILESEXTRAPATHS_append
- SRC_URI overrides
Best practices:
- Keep all patches inside
meta-everos/recipes-*/<recipe>/<version>/ - Avoid renaming upstream patch files
- Never overload
FILESEXTRAPATHSin machine configs
Isolate everything.
E. Use Layer Priority Intentionally (But Avoid Overuse)
BBFILE_PRIORITY helps you control overrides.
Use it sparingly:
meta-raspberrypishould not be outranked by accidentmeta-everosshould override only userland components- Kernel and bootloader remain untouched unless explicitly overridden
Most breakage comes from implicit priority decisions, not explicit ones.
5. Real-World Usage: How This Model Helps a Multi-Device Ecosystem
In Hoomanely’s multi-device architecture, consistency matters:
- A tracker using lightweight LoRa telemetry
- An EverBowl deriving behavior insights from sensors and edge vision
- An EverHub aggregating and processing data at home
Different hardware. Different workloads.
The same base OS.
Because our layering model is:
1. Predictable
Adding a new machine config never breaks an existing one.
2. Portable
Switching SoM families doesn’t require rewriting our distro.
3. Scalable
New services, new sensors, new pipelines drop cleanly into meta-everos.
By keeping CM4 BSP logic fully contained in meta-raspberrypi, we avoid kernel surprises and bootloader drift.
By isolating product logic in meta-everos, we keep device behavior consistent even when underlying hardware evolves.
This is the only way to build a long-lived embedded platform.
Visual Placeholder #3: “Cross-Device Consistency Map”
A 3-branch diagram:
- Left: Tracker (motion, barometer, LoRa/GPS)
- Center: EverBowl (vision, sound events, temp, weight)
- Right: EverHub (edge compute)
All three feed into a common EverOS Layer (meta-everos) which sits above meta-raspberrypi BSP.
Annotations:
- “Shared policies”
- “Consistent logging + OTA behavior”
- “Predictable filesystem + services”
Dark-mode, sleek vectors.
6. Takeaways: Principles for a Future-Proof Yocto Layering Model
Here are the key lessons that keep Yocto predictable:
1. Treat BSP as a dependency, not a playground.
Don't fork CM4 BSP behavior unless you fully understand the impact.
2. Keep product logic in your own layer.
meta-everos is where application-level decisions live.
3. Machine configs should be minimal and pure.
Only describe the hardware, nothing else.
4. Avoid bbappend overuse.
Each one is a foot-gun unless clearly intentional.
5. Use layer priority intentionally.
Never allow accidental overrides.
6. Design for multiple SoMs from the start.
Even if you only build CM4 today, tomorrow will be different.
7. The best Yocto setup is the one that doesn’t surprise you.
Predictability beats cleverness, always.
This is how we build a clean, stable, scalable OS foundation across Hoomanely’s pet-care device ecosystem—and it’s a model you can adopt for your own embedded systems.





